Introduction
Predatory publishing refers to exploitative publishing practices that prioritize profit over scholarly integrity. These publishers often mislead authors with false claims of peer review, indexing, or impact, while charging high fees for publication.
Understanding how to identify and avoid predatory journals is essential for protecting your research reputation and ensuring your work is disseminated responsibly.
Predatory Journal
What Are Predatory Journals?
Predatory journals:
-
Claim to be peer-reviewed but do not follow rigorous editorial standards.
-
Solicit manuscripts aggressively via spam emails.
-
Charge authors publication fees without providing legitimate editorial or publishing services.
-
Provide misleading information about indexing, editorial boards, and impact factors.
Red Flags of Predatory Publishers
- Unsolicited Invitations: Frequent, generic emails inviting you to publish or join editorial boards.
- Mass Mailings: Messages are not personalized — they might address you as “Respected Researcher” or “Dear Scientist”.
- Poorly Written Messages: Emails may contain grammatical errors, awkward phrasing, or overly flattering language (e.g., “We admire your excellent contribution in science…”).
- Questionable Peer Review: Very rapid acceptance or vague review process.
- Pressure Tactics: They often emphasize urgency (“Submit within 7 days for rapid publication”).
- Too Broad in Scope: Journals claim to publish everything from nanotechnology to medieval history in one venue.
- Unclear Fees: Hidden or excessive article processing charges (APCs).
- Misleading Indexing Claims: Claiming inclusion in databases like Scopus or Web of Science when not true.
- Fake Metrics: Use of fake or obscure impact factors (e.g., “Global Impact Factor”).
- Poor Website Quality: Broken links, spelling errors, or suspicious journal titles mimicking reputable ones.
- Dubious Editorial Board: Board members with no credentials, fake names, or scholars unaware of their listing.
- Free email services: Gmail, Yahoo, Hotmail, Outlook, etc. Legitimate journals almost never use @gmail.com for official correspondence.
- Misspelled or lookalike domains:
- Example: @springer-journal.net (instead of @springer.com). @elsevierpublication.org (Elsevier actually uses @elsevier.com).
- Overly generic domains: @editorialoffice.org, @globaljournals.info, @sciencepublication.net.
- Mismatch with the website: The journal’s website says one thing, but the editor emails from a completely different or free domain and provides mismatched information.
- Fake or Misleading Addresses: They may list a prestigious location (e.g., London, New York, Geneva) but actually operate elsewhere. Sometimes the listed address is a P.O. Box, virtual office, or even a residential building.
- Multiple “Headquarters” - A single journal might claim offices in USA, UK, Dubai, India, and Nigeria simultaneously. Legitimate publishers usually have one clear headquarters and a few global branches.
- Vague or Missing Contact Information: Only a generic contact form with no physical address. No phone number or institutional affiliation provided.
- Suspicious Geographic Patterns: Many predatory publishers are based in regions with less regulatory oversight but claim global prestige. Overuse of terms like “International,” “Global,” or “World” in journal titles can sometimes be a giveaway
How to Evaluate a Journal?
Use these strategies to assess journal quality:
-
Check trusted databases:
-
Directory of Open Access Journals (DOAJ)
-
Journal Citation Reports (JCR)
-
Scopus
-
-
Consult whitelists & blacklists:
-
Think. Check. Submit. checklist
-
Cabells Journalytics vs. Predatory Reports
-
-
Examine policies: Look for clear peer review, archiving, and retraction policies.
-
Ask colleagues or librarians: Get expert input before submission.
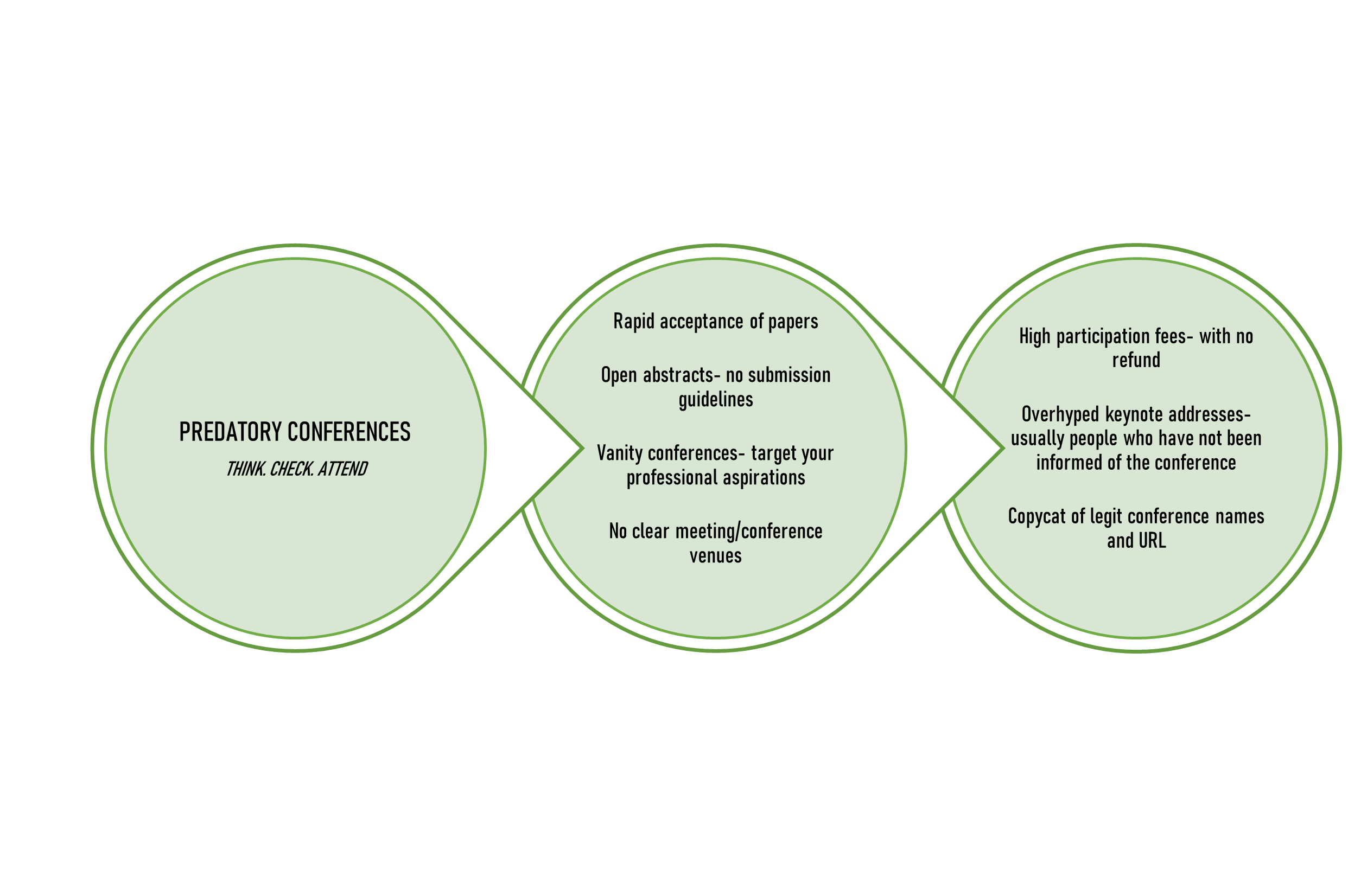
Predatory Conferences